西北农林科技大学信息化管理处(网络与教育技术中心)-j9九游会真人
一、漏洞概述
微软在2021年6月的安全更新中修复了其windows操作系统后台打印服务windows print spooler的远程代码执行漏洞(cve-2021-1675),windows print spooler管理所有本地和网络打印队列,控制所有打印工作。攻击者利用该漏洞可绕过安全检查在目标设备上安装恶意驱动程序。鉴于漏洞危害较大且相关漏洞利用代码已公开,建议相关用户尽快采取措施进行防护。
二、影响范围
windows server 2012 r2 (server core installation)
windows server 2012 r2
windows server 2012 (server core installation)
windows server 2012
windows server 2008 r2 for x64-based systems service pack 1 (server core installation)
windows server 2008 r2 for x64-based systems service pack 1
windows server 2008 for x64-based systems service pack 2 (server core installation)
windows server 2008 for x64-based systems service pack 2
windows server 2008 for 32-bit systems service pack 2 (server core installation)
windows server 2008 for 32-bit systems service pack 2
windows rt 8.1
windows 8.1 for x64-based systems
windows 8.1 for 32-bit systems
windows 7 for x64-based systems service pack 1
windows 7 for 32-bit systems service pack 1
windows server 2016 (server core installation)
windows server 2016
windows 10 version 1607 for x64-based systems
windows 10 version 1607 for 32-bit systems
windows 10 for x64-based systems
windows 10 for 32-bit systems
windows server, version 20h2 (server core installation)
windows 10 version 20h2 for arm64-based systems
windows 10 version 20h2 for 32-bit systems
windows 10 version 20h2 for x64-based systems
windows server, version 2004 (server core installation)
windows 10 version 2004 for x64-based systems
windows 10 version 2004 for arm64-based systems
windows 10 version 2004 for 32-bit systems
windows 10 version 21h1 for 32-bit systems
windows 10 version 21h1 for arm64-based systems
windows 10 version 21h1 for x64-based systems
windows 10 version 1909 for arm64-based systems
windows 10 version 1909 for x64-based systems
windows 10 version 1909 for 32-bit systems
windows server 2019 (server core installation)
windows server 2019
windows 10 version 1809 for arm64-based systems
windows 10 version 1809 for x64-based systems
windows 10 version 1809 for 32-bit system
三、防护措施
已开启windows自动更新的系统会自动安装补丁,无需手动更新升级。未开启自动更新的计算机及所有windows服务器按照以下方法做好防护。
1.安装补丁
目前,微软官方已针对支持的系统版本发布了修复该漏洞的安全补丁,官方补丁下载地址:。
由于网络问题、计算机环境问题等原因,windows update的补丁更新可能出现失败。用户在安装补丁后,应及时检查补丁是否成功更新。
右键点击windows图标,选择“设置”,选择“更新和安全”-“windows更新”,查看该页面上的提示信息,也可点击“查看更新历史记录”查看历史更新情况。
针对未成功安装的更新,可点击更新名称跳转到微软官方下载页面,建议用户点击该页面上的链接,转到“microsoft更新目录”网站下载独立程序包并安装。
2.临时应对措施
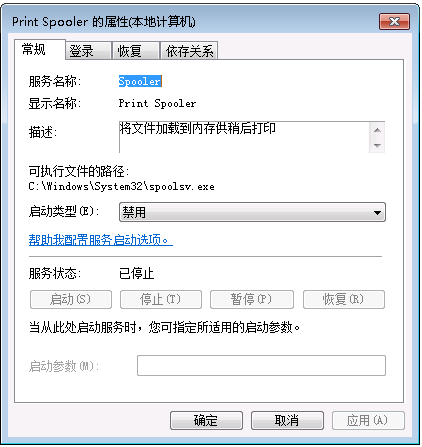
若无法成功安装补丁,则可通过禁用print spooler服务来进行缓解:
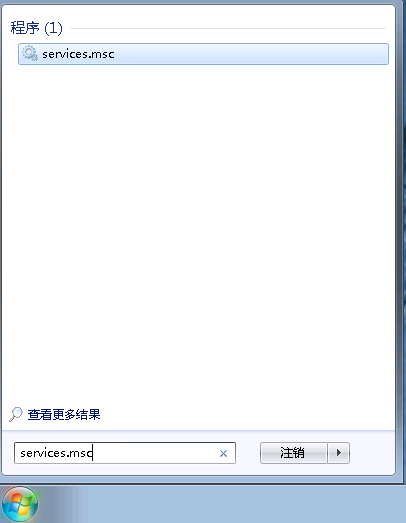
(1)单击windows图标或搜索框,搜索“services.msc”,在服务应用中找到print spooler服务。
(2)双击“print spooler”,停止运行服务,同时将“启动类型”修改为“禁用”。